Litigation holds can retain mailbox data, but that’s it. You can swap litigation holds out for a Microsoft 365 retention policy and gain extra functionality, such as retaining OneDrive for Business content for the mailbox owners. It’s easy to script the transition from litigation holds to retention policy using PowerShell and to show how, we include a fully working script.
Microsoft recently announced the deprecation of the Exchange cmdlets to search for mailbox audit data. The audit data is ingested into the Microsoft 365 unified audit log, but it’s more difficult to find and retrieve Exchange mailbox audit events. Methods are available to find mailbox audit data, but interpreting what comes back is different. Any script that depends on the old cmdlets must be updated to interact with the unified audit log.
Litigation holds were great when introduced with Exchange 2010. Fifteen years on, better methods exist to preserve user information, like eDiscovery holds. It might seem unnatural to move from litigation holds to eDiscovery cases, but this approach allows the preservation of both mailbox and OneDrive content for as long as necessary. Retention policies can serve the same purpose, so choice exists for modern preservation.
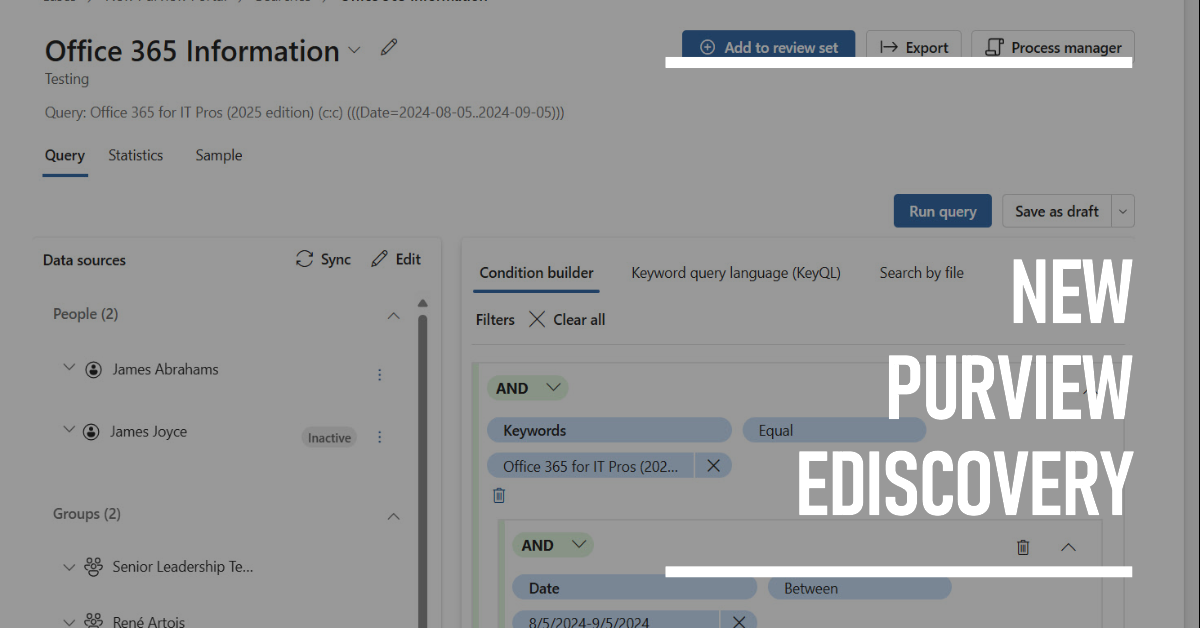
Microsoft is making some important changes to Purview eDiscovery from May 26, 2025. The changes affect how content searches work and are likely to affect many Microsoft 365 tenants. Administrators and eDiscovery investigators will both have to master new ways of working with eDiscovery cases, searching for information, reviewing search results, and exporting what’s found. Changes to PowerShell cmdlets might affect scripts, so there’s lots to consider.
Microsoft Purview makes it easy to apply sensitivity labels to Office documents and PDF files with auto-label policies. Licenses are needed for auto-label policies, but at what cost? We look at the various licenses available to cover the functionality and consider if a DIY approach using the Graph API to apply labels would be cost effective.
The Microsoft E5 Security add-on is available for Microsoft 365 Business Premium (and other) tenants. The add-on looks like a bargain because the bundle offers significant value over individual licenses, but is it really? Like everything in life, unless you can use something, there’s no point in having it. In this case, have a plan to use E5 Security to deliver measurable results before you hand over any more license revenue to Microsoft.
Often Microsoft 365 tenants have large numbers of old but confidential documents that they need to protect and stop Microsoft 365 Copilot finding. Auto-label policies and trainable classifiers can apply sensitivity labels to protect Office files from Microsoft 365 Copilot using the DLP policy for Copilot. It’s a great example of combiining Microsoft 365 features to achieve a goal.
File sharing is at the heart of SharePoint Online. Being able to report file sharing events by analyzing the audit log is a good skill for Microsoft 365 tenant administrators to have. It allows administrators to know who shared what with whom and if the information being shared is protected adequately with sensitivity labels. But reporting file sharing is not just a matter of retrieving audit events. Work is necessary to refine and extract the goodness from the data.
A reader asked if it’s possible to discover who made retention label assignments for SharePoint files. The Files Graph API can’t tell you who (or what policy) made retention label assignments, but it’s possible to find this information in the audit log and use that data to report the requested information. All with a few lines of PowerShell!
The DLP policy for Microsoft 365 Copilot blocks access to sensitive files by checking for the presence of a sensitivity label. If a predesignated label is found on a file, Copilot Chat is blocked from using the file content in its responses. The nicest thing is that the DLP policy prevents users knowing about sensitive information by searching its metadata.
There’s no doubt that SharePoint Online sites and OneDrive for Business accounts hold lots of old files. A new On Demand Classification PAYG service aims to find and classify that data and apply sensitivity and retention labels based on policy settings. It’s a good idea for tenants that has these kinds of cold files hanging around gathering dust without anyone knowing if any of the files hold confidential information.
Microsoft has announced the removal of events alerts from the Purview Audit solution. Fortunately, the decision doesn’t affect activity alerts. Audit-based activity alerts are a way for tenants to mark events that they want to be notified about through email when these events appear in the unified audit log. Although they remain available, better ways exist to monitor critical audit events. The only problem is deciding which approach to take.
This article describes how to use Azure Automation for audit searches. The runbook runs an audit search to find events for specific operations, refines the set of events found by the search, and sends the information by email. Hopefully, someone will respond to the message and do the right thing to check the insight derived from the events.
On December 12, Microsoft said that they want to make the Search-UnifiedAuditLog cmdlet use high completeness for all its searches. If implemented, the result will be a disaster because many of the current uses of the cmdlet to retrieve audit log data will be rendered impracticable because of the slowness and unreliability of high completeness searches. Microsoft just doesn’t seem to understand how its software is used in production.
This article describes how to report the audit events for a user over a single day. The task seems simple, but inconsistency in audit payloads makes it harder. Workloads don’t help by the variations in audit events. In any case, persistence and knowledge about what the audit event captured for an action helps to decode the data, as illustrated by the script detailed here.
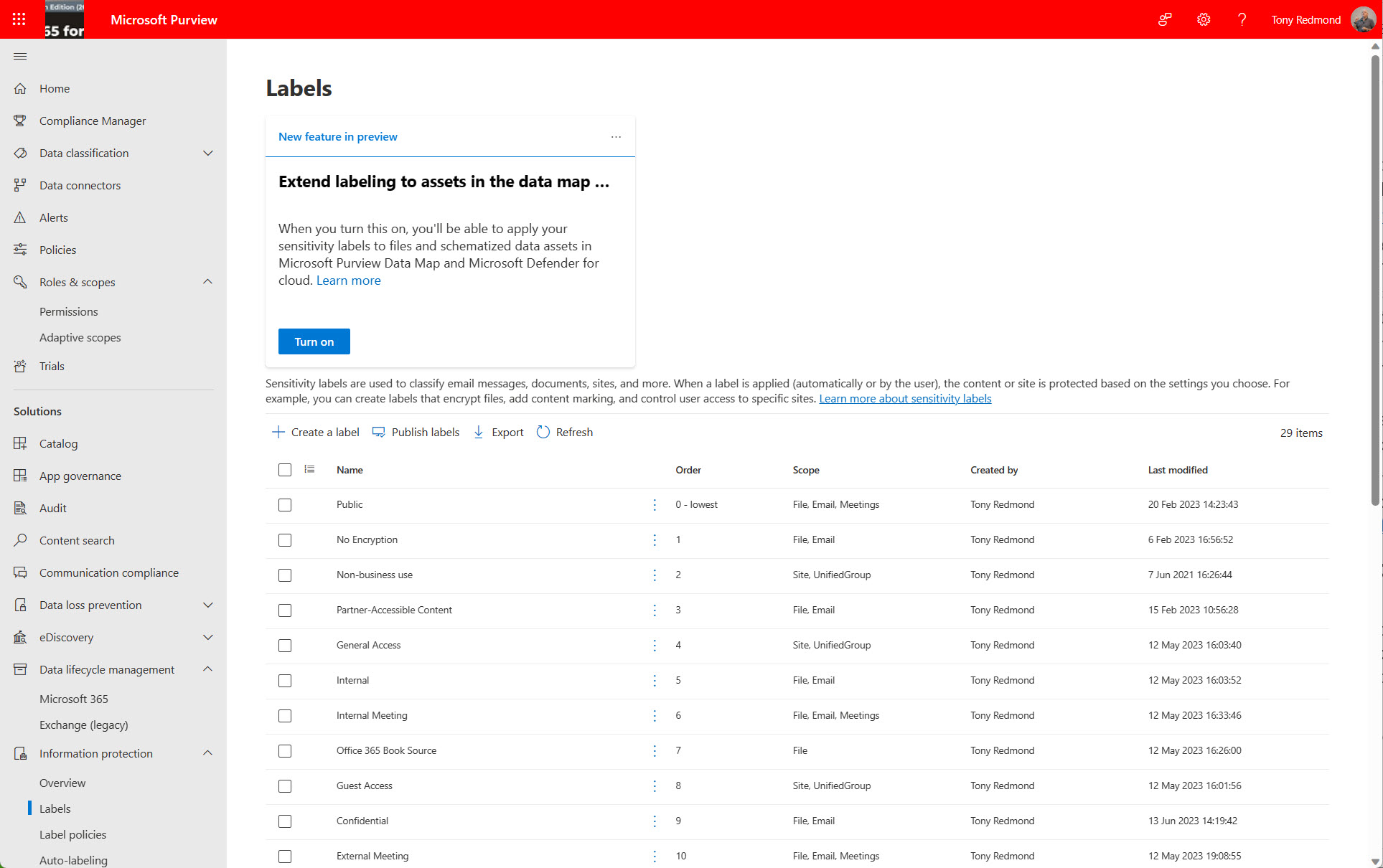
Microsoft recently renamed the default set of sensitivity label permissions. Each permission defines the usage rights for a labelled item for users. The rights range from the basic actions like edit, save, and print to the more advanced extract, right to run macros, and export. The trick is to make sure that sensitivity labels assign the right permissions to users.
The Purview Insider Risk Management solution can do all sorts of clever things, like tracking sensitivity label downgrades and removals as an indicator that a user might be preparing to exfiltrate data. The same kind of checking can be done by using the events captured in the audit log when people remove or change sensitivity labels. All in a few lines of PowerShell…
In a November 8 post, Microsoft says that Purview Data Lifecycle Management will allow tenants to split processing of Copilot interactions and Teams chats with different policies. The public preview for the change should be available in mid-November. This update makes perfect sense because there’s no logic to dictate that Microsoft 365 tenants want to impose the same retention period for Teams chats and Copilot interactions.
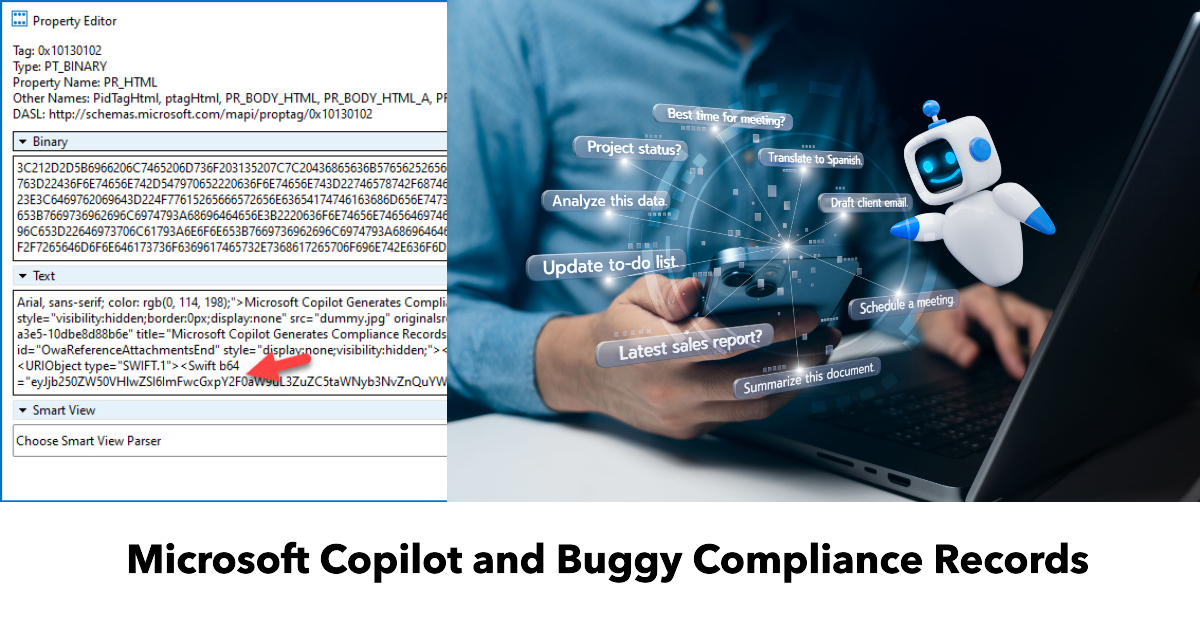
A recent article about analyzing interaction records for Microsoft 365 Copilot led to the question if it’s possible to do the same for Microsoft Copilot. After checking the compliance records captured by the Microsoft 365 substrate, we discovered that Microsoft Copilot generates compliance records. However, a bug with encoded text means that the information captured for responses from Microsoft Copilot and Microsoft 365 Chat isn’t visible. All explained here.
A reader asked how to find emails with sensitivity labels. Everyone knows that you can find SharePoint files protected by sensitivity labels, but what about emails? MAPI properties exist that hold details of sensitivity labels. These properties are promoted to Microsoft Search, and this allows features like end-user searching through the Microsoft 365 app and Outlook to work. But the best way to find emails with sensitivity labels is to use a Purview content search.
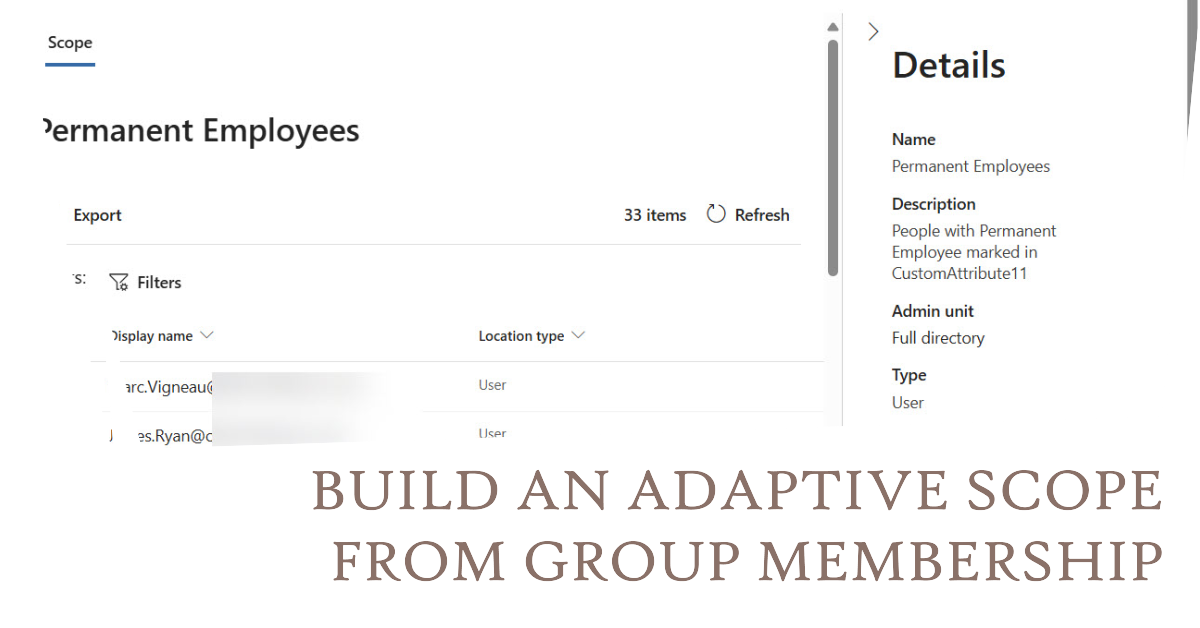
Adaptive searches are a nice way to target users, sites, and groups for Purview retention processing. But a user adaptive scope can’t select members of a group and target them. That is, unless you use the same attribute to identify users for both a dynamic group and an adaptive scope, which is what’s explained here.
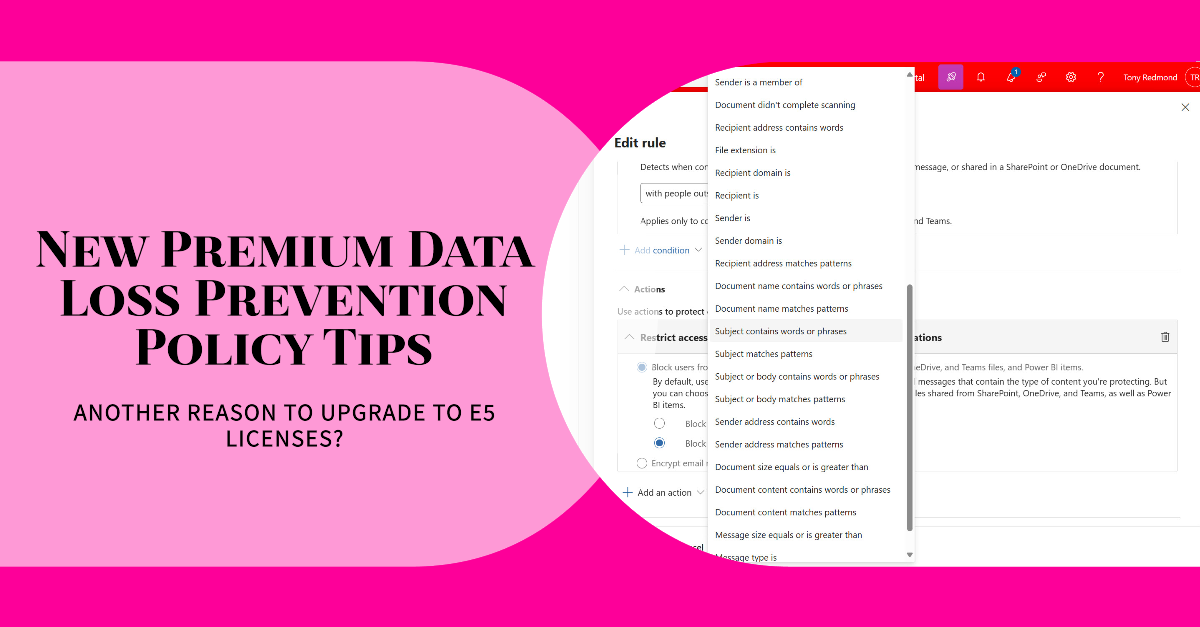
MC894577 announces that DLP policy tips displayed in Outlook will soon support a set of new conditions. That’s good, but the text of the announcement is unclear about important points like the clients that will support the new policy tips, what kinds of groups are supported by the conditions, and precise details of how Outlook will differentiate between users with Office 365 E3 and E5 licenses.
eDiscovery is a calling best left to skilled investigators. But Microsoft 365 administrators need to know how to search and how the new Purview eDiscovery works. The new implementation is due by the end of 2024 and is in preview now. It unifies the three existing solutions in the Microsoft 365 eDiscovery space and promises to deliver new functionality. But will it make its dates? Who knows!
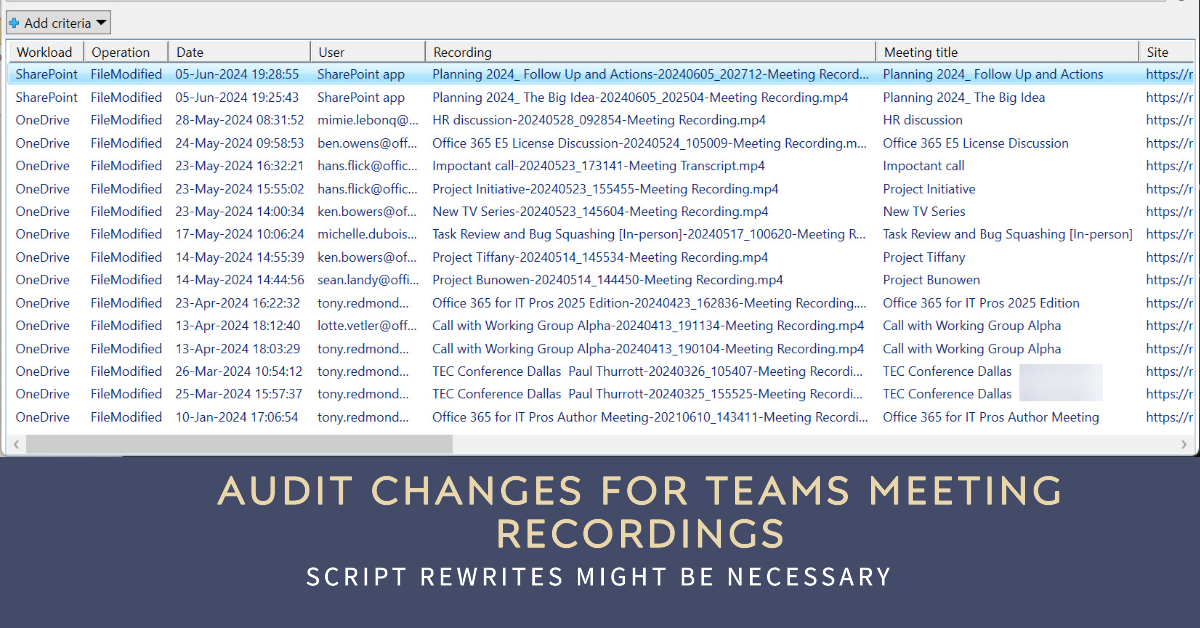
Three years ago, I wrote a script to analyze the audit records generated for Teams meeting recordings. Then things changed in terms of how the audit records were generated and how the Search-UnifiedAuditLog cmdlet returns audit search results. All of which meant that considerable work was needed to revamp (rewrite) the script. Maybe you need to check any script that uses the Search-UnifiedAuditLog cmdlet too?
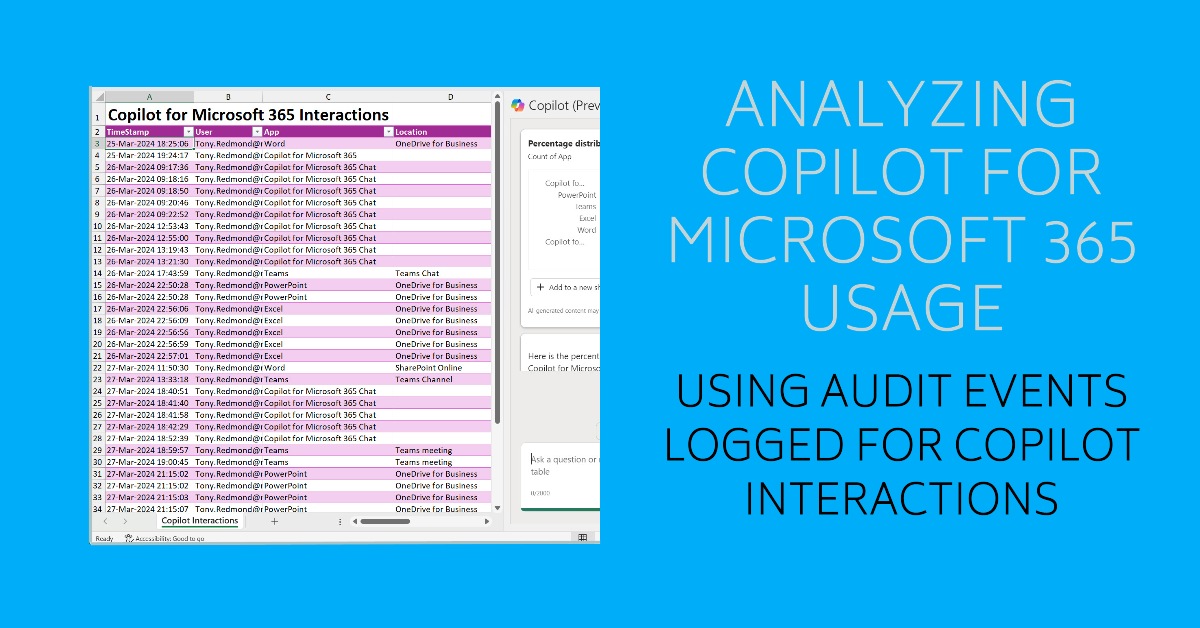
The unified audit log includes Copilot for Microsoft 365 audit events captured when users interact with Copilot through apps. The information is very helpful in terms of understanding the usage of Copilot in different apps (apart from Outlook, which isn’t captured). Some care needs to be taken to understand the data and interpret the audit events, but that’s usual when dealing with Microsoft 365 audit data.
A new preview feature supports high completeness audit log searches. These searches are optimized to make sure that they find every matching audit instead of finishing as quickly as possible. High completeness audit log searches do take more time but their results are accurate and they find more records than Search-UnifiedAuditLog was able to in the past. Looks like a good new feature.
A January 26 post announces the deprecation of four old Exchange audit cmdlets in favor of the Search-UnifiedAuditLog cmdlet. Removing old cmdlets is fine, but it would be nice if Microsoft took the opportunity to make Search-UnifiedAuditLog work better. Too many inconsistencies exist in how workloads provide information in audit events and Microsoft has made some recent unannounced changes.
In message center notification MC703706 Microsoft announces yet another attempt to retire the Search-Mailbox cmdlet. This time it’s due to happen in March 2024. I don’t mind Microsoft removing old technology from its products, but it’s important that the old functionality is replaced by newer, better technology. And that’s not the case here. At least, not so far.
The Sensitive by Default control allows tenants to prevent external access to newly uploaded documents until DLP processing checks their content. The idea is to close off the opportunity external users have to access control between its upload and DLP scanning of the content. You can combine the sensitive by default control with sensitivity labels to exert maximum control over confidential material.
Microsoft plans to make an eDiscovery hold report available to tenants in January 2024. This article explains how to use PowerShell to create a similar report. Without seeing what Microsoft plans, it’s hard to create a perfect replica, but it will be possible to upgrade the script once Microsoft reveals their hand.
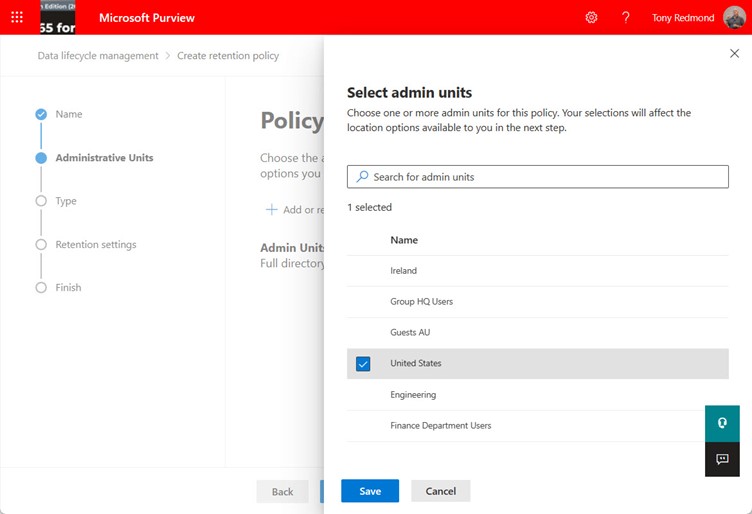
Entra ID administrative units are supported for granular access to the Microsoft 365 audit log. Exchange Online manages the audit log so it’s core to the support. This article reviews how to restrict access to the audit log using compliance roles and RBAC and how administrative unit data is stamped onto audit events during ingestion to support restricted searches based on administrative units.
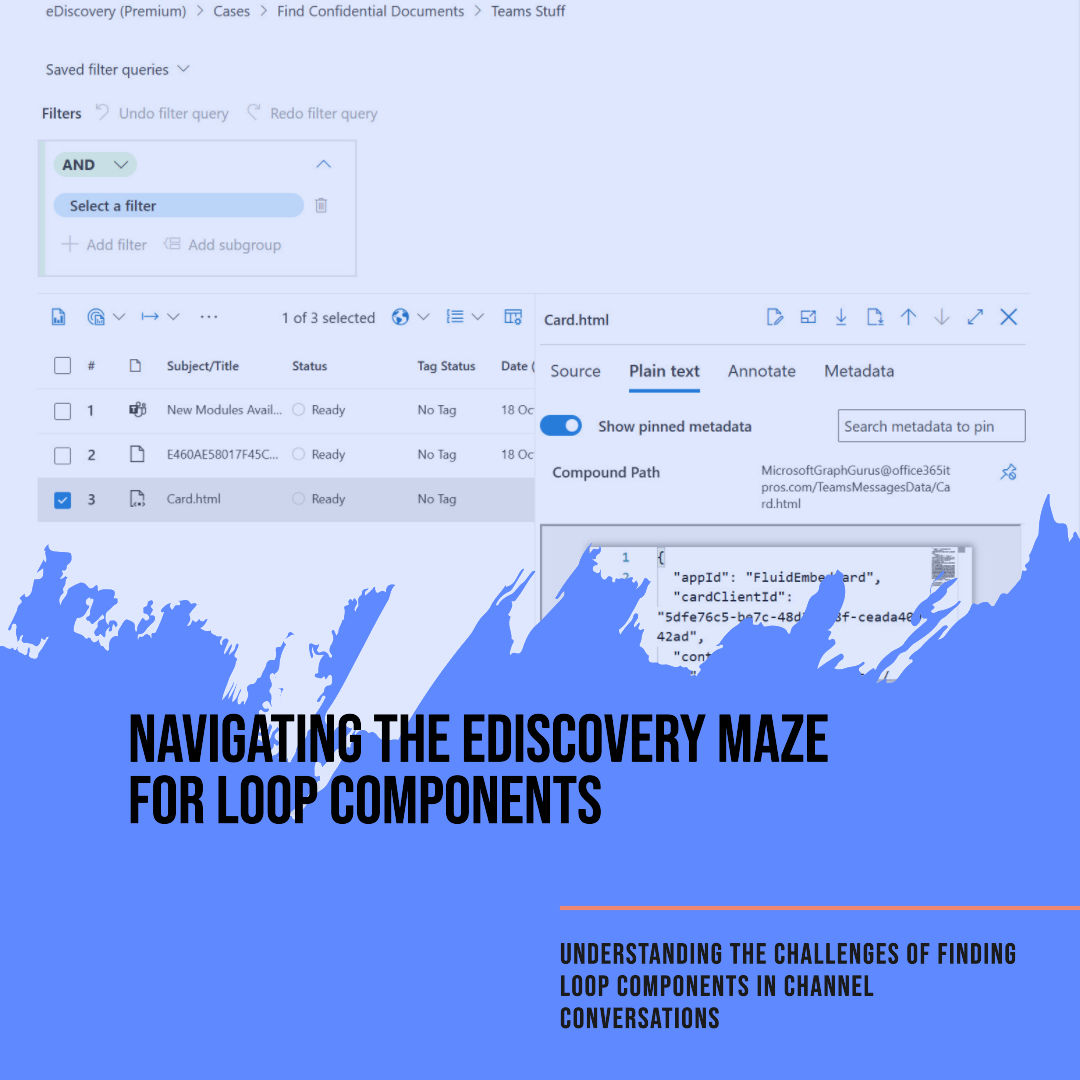
Following new support of Loop components for Teams channel conversations, it’s sad to discover that Loop component eDiscovery remains challenging two years after the first appearance of component technology in a Microsoft 365 application. eDiscovery can certainly find Loop components, but creating a seamless picture about their usage is harder than it should be.
A question about finding out which sensitivity label policy makes a label available to a user requires some PowerShell to figure out the answer with some human-friendly results. The outcome is a script that analyzes sensitivity label policies to find where a user gets their labels from. It’s another example of how useful PowerShell can be.
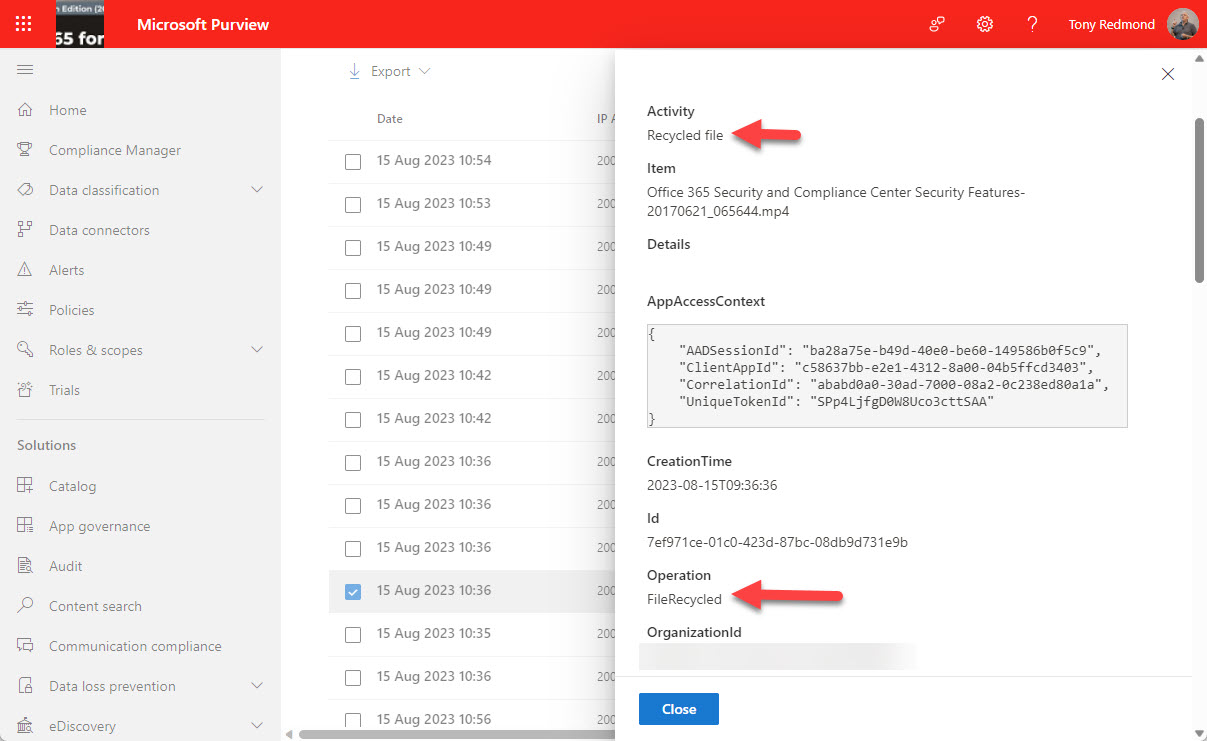
For years, I have scanned the audit log to find FileDeleted events to report deletions of SharePoint and OneDrive documents. Now, FileRecycled audit events are used instead. This wouldn’t be a problem if Microsoft had told customers, but not a trace can be found to let organizations know that the audit data they use for compliance operations has changed. I don’t know if this is the only activity name change, but given that one update has happened (and for a relatively important audit event), it’s likely that others lurk in the undergrowth.
Microsoft has announced that they are replacing the user data search tool with Purview eDiscovery standard. The change will happen on 30 August 2023 and active user data search cases will be transferred automatically to eDiscovery standard at that point. The change makes sense because the user data search tool hasn’t been enhanced much since its inception. Anyway, user data search cases were simply a special form of eDiscovery case, and now they’re all the same.
The SharePoint Preservation Hold Library is where files needed for retention or hold purposes are stored. In the past, the library stored separate copies of each version of a retained file. Now it stores files complete with the entire version history, which is more intelligent and means that SharePoint consumes less storage for retention.
The need to find SharePoint documents with sensitivity labels might arise during a tenant divestiture to decrypt the documents before the split. As it turns out, searches against the SharePoint InformationProtectionLabelId property is a good way to find the files. After that, the need arises to decrypt the documents, which is where Microsoft Purview eDiscovery (premium) might come in handy.
Microsoft Purview data lifecycle management (retention labels and policies) support Azure AD administrative units to scope the set of objects that compliance administrators can manage. Administrative units can be used with data lifecycle management, data loss prevention (DLP), and information protection (sensitivity labels). You’ll need Microsoft 365 E5 licenses (or equivalents) to manage the policies, but that shouldn’t be an issue for the kind of enterprise tenants Microsoft is targeting this functionality at.
Following the removal of Remote PowerShell connections for Exchange Online, Microsoft is removing Remote PowerShell for the compliance endpoint. The change to REST-based cmdlets is expected to deliver better performance and reliability. The changes are implemented in V3.2 of the Exchange Online management module, which should be available on May 1.
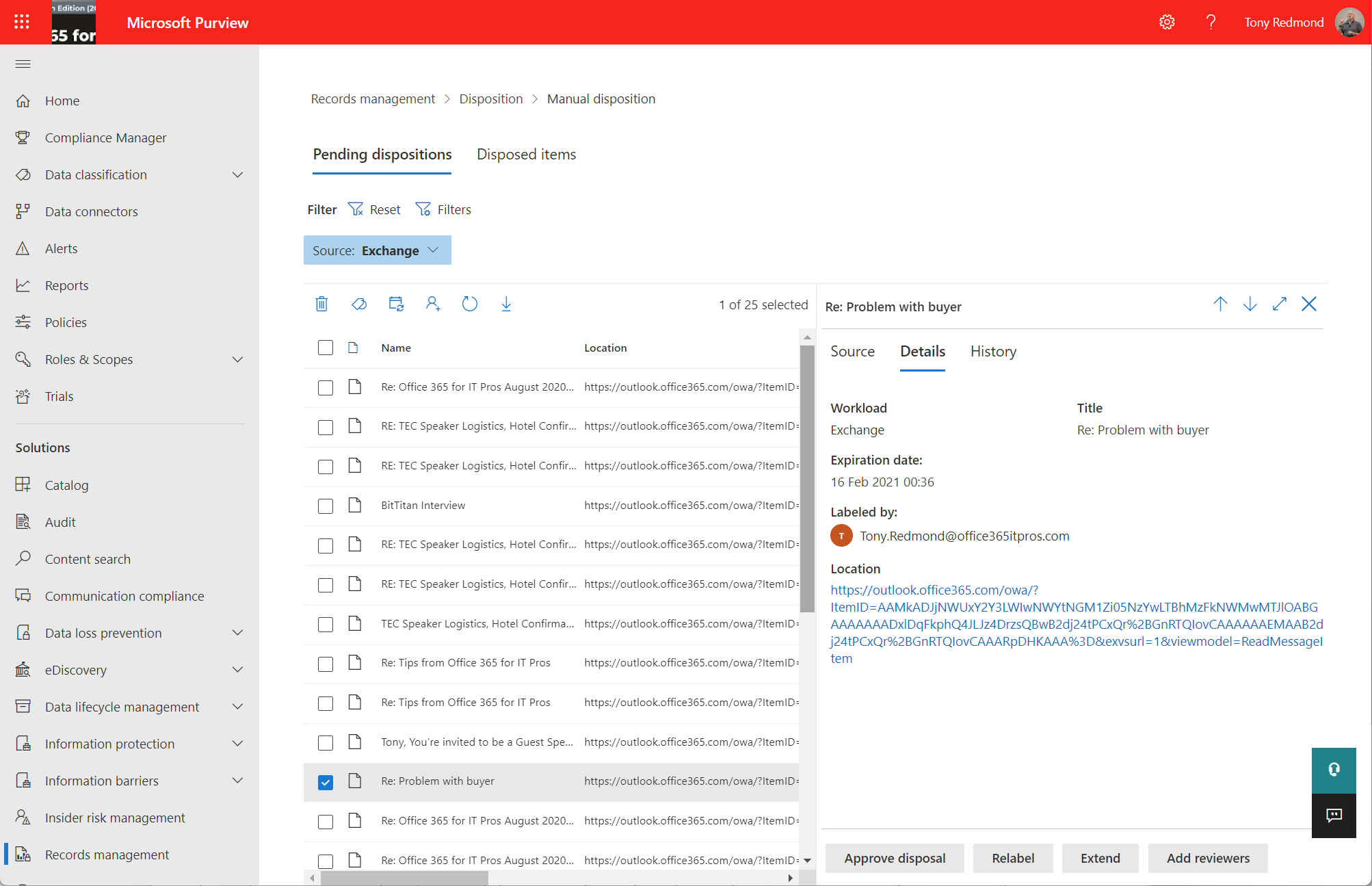
The Get-ReviewItems cmdlet (in the Exchange Online management module) is available to export details about disposition review items in either a pending or disposed state. It’s possible that you don’t care very much about records management, retention labels, or disposition processing, but if you do, you’ll be glad that the new cmdlet exists.