In July, Microsoft plans to introduce an app consent policy to stop users granting access to third-party apps to their files and sites. Letting users grant unsupervised consent to third-party apps to access files stored in OneDrive for Business and SharePoint Online is a bad idea. There are certainly apps out there that need such access, but requiring one-time administrator approval is no hardship.
Microsoft 365 tenants with Entra P1 or P2 licenses can use a custom banned password list to stop people using specific terms in their passwords. The idea is to prevent easily-guessed terms being used in passwords. You could also block words deemed to be objectionable. In any case, this article explains how to maintain the custom blocked password list with a PowerShell script.
The last thing you want on a Saturday morning is to find that Entra ID has blocked your account because of leaked credentials. Even though the account is protected by MFA, it’s still important to remediate the event by changing its password. A check against some beta sign-in metrics shows that no one has tried to use the leaked credentials, so that’s good.
Entra ID populates the sponsor property for new guest accounts with details of the person who invites the guest to the tenant. It’s data that can be used for different purposes, such as having someone to justify the continued presence of a guest account in a Microsoft 365 tenant. This article explains how to report guest accounts and their sponsors with some straightforward PowerShell.
Microsoft will disable service principal-less authentication in March 2026. This step closes a hole that doesn’t exist today but might in the future. The strange thing is that many Microsoft 365 applications seem to use service principal-less authentication. Microsoft will take care of first-party apps before March 2026, but there’s work to do for apps from other vendors.
A new preview option in the Entra admin center supports the ability to update multiple Entra ID accounts. You can update properties, add managers and sponsors, update group membership, revoke account access, and so on. The only surprising thing about the new option is that it’s taken Microsoft so long to add it to the admin center.
An article about the horrible devastation that an attacker can wreak inside a compromised Microsoft 365 tenant highlighted how protected actions can help by preventing attackers from being able to permanently remove user accounts unless they can pass additional authentication tests. Protected actions won’t stop attackers that have complete control over a tenant, but it might irritate them!
A new people administrator role is available in Entra ID. The new role allows holders to manage settings associated with people, like pronouns and custom properties for the Microsoft 365 user profile card. The people administrator role is a less privileged way to assign responsibilities for people actions and removes the need to assign more privileged roles like User administrator. Time for a role review!
Entra ID retains audit log records for service principal signins for 30 days. The audit data can reveal some interesting insights such as the presence of unexpected service principals or access to an application from an external source, or even the use of an app secret by an application instead of a more secure method. It’s time to write some PowerShell to interpret the data.
Entra ID allows unprivileged users to update the user principal name for their accounts via the admin center or PowerShell. It seems silly because no justification for allowing people to update such a fundamental property is evident. Perhaps Microsoft has some excellent logic for allowing such updates to occur, but blocking access seems like the right thing to do.
After many twists and turns since August 2021, the MSOnline module retirement will happen in April 2025. The AzureAD module will then retire in the 3rd quarter. It’s way past time to upgrade PowerShell scripts. The question is whether to use the Entra module or the Microsoft Graph PowerShell SDK. I know which option is best and say why in this article.
Service principal sign-in activity is a new insight available in the Entra admin center. As explained here, it’s also possible to use PowerShell to fetch and analyze the data to derive new insights into what apps create service principals in a tenant and what organizations own the apps. Some detective work is needed to fully understand the data. That might be an ongoing task, but at least we have the data.
This article describes how to create eligible and active PIM role assignment requests using cmdlets from the Microsoft Graph PowerShell SDK. Although the PowerShell code is straightforward, Microsoft recommends using the Entra admin center for Privileged Identity Management. But you can automate the management of role assignment requests if you want to.
Microsoft recommends that developers move from the older DirectoryRoles Graph API and use the UnifiedRoleDefinition API instead. Changing APIs will impact the code in any PowerShell scripts used to automate role assignments. In this article, we review some examples of the older way to assign roles and show how to do the same tasks with the new API.
A reader asked why the Entra admin center includes an option to manage per-user MFA settings for accounts. I don’t know why Microsoft added this option, but it doesn’t take away from the strategy to enforce and manage multifactor authentication through conditional access policies. Microsoft has been very focused on CA policies for the last few years and per-user MFA will eventually be subsumed into the CA strategy.
Many articles describe how to disable a service plan for a product license assigned to a Microsoft 365 account, but few cover how to enable service plans should the need arise afterward. This article covers the basics of disabling and enabling service plans for Microsoft 365 licenses using PowerShell, including the very important step of finding existing disabled plans. Everything’s easy once you know how.
Directory synchronization features control how the Entra Connect tool works when synchronizing accounts from Active Directory to Entra ID. The current advice is to use a cmdlet from the depreciated MSOL module to update settings. This article explains how to do the job with the Graph APIs, including cmdlets from the Entra PowerShell module.
A recent question asked how to force users to reauthenticate at 7AM every Monday. The solution seems to revoke access for user accounts. This article describes how to create an Azure automation runbook (PowerShell script) to find target accounts and revoke their access. By linking the runbook to an automation schedule, we can make sure that revocation happens at the desired time.
Container management labels are an effective way to ensure that groups, teams, and sites have the right settings. The Graph doesn’t support custom attributes for groups, so these attributes aren’t available to store details of the “approved” container management label to check if anyone has changed the label after the original assignment. Time to find a new way to store this data.
The Maester tool is a great way to get a security assessment for a Microsoft 365 tenant. Being able to create custom Maester tests makes it even better. In this article, we explain how to create a custom Maester test that reads the Entra ID Groups policy to report if users are allowed to create new Microsoft 365 groups (and teams).
A new Entra ID photo update settings policy aims to cure the mish-mash of existing settings controlling how user profile photos are updated in Microsoft 365. The new policy is based on a Microsoft Graph resource. Work is needed to update clients to respect the policy settings and take over from current controls, like the OWA mailbox policy.
The ability to restore deleted groups only covers Microsoft 365 groups. That’s an odd situation to be in given the different types of groups in Microsoft 365, and the reasons why things work (or don’t) the way they do is down to history and different teams within Microsoft. It’s logical that customers assume they can restore any type of deleted group. Microsoft needs to do some magic to make that assumption real.
A recent report highlighted the problem of on-premises accounts synchronized to Entra ID that receive administrative role assignments. This article explains how to report the administrative role assignments managed by Privileged Identity Management (PIM) or direct role membership so that it’s easy to highlight on-premises accounts holding administrative roles.
V1.2 of the User Passwords and MFA report includes the names of authentication methods registered for user accounts. V1.3 expands the amount of detail reported for each method, such as the phone number used for SMS challenges, or the email address used for SSPR. It’s a small but important detail that’s useful to administrators. However, it also comes with a potential privacy issue, so the script must handle that too.
A Microsoft Graph update makes per-user MFA state available for user accounts. Being able to access the data means that we can include it in the User Passwords and Authentication report. You can now see if accounts are disabled, enabled, or enforced for per-user MFA along with all the other information captured about passwqrd changes, MFA authentication methods, and so on.
This article describes how to use the Microsoft Graph PowerShell SDK to report delegated permission assignments to user accounts and apps. Like in other parts of Microsoft 365, the tendency exists to accrue delegated permissions for both user accounts and apps over time. There’s nothing wrong with having delegated permissions in place, if they are appropriate and needed – and that’s why we report their existence.
This article describes the process of blocking device code authentication requests against Entra ID with a preview feature for conditional access policies. It’s a good idea to tighten tenant security by removing device code authentication unless a clearly-defined need exists for apps to authenticate using this method. I suspect that most tenants will find that they can happily do without device code authentication.
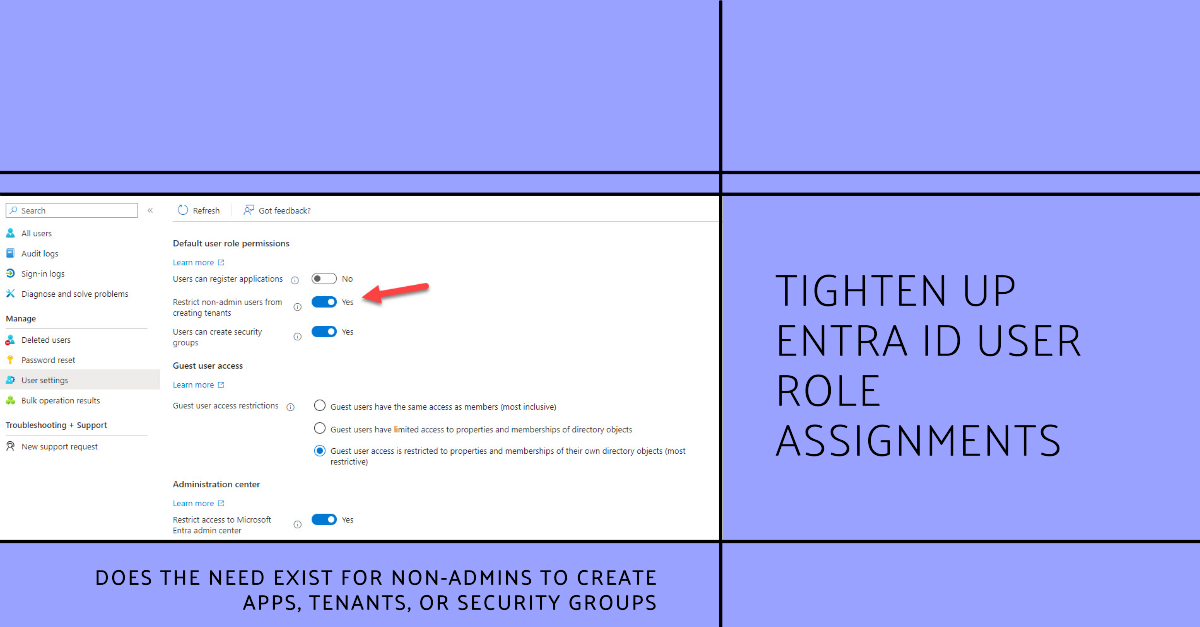
The user authorization policy defines user role permissions, or actions that non-admin users can take within an Entra ID tenant. The default settings are silly. I can’t think of good reasons to allow non-admin users to create new registered apps, tenants, or security groups. Why default settings allow these actions is a mystery, and it could be they’re just outdated.
In a May 2 announcement, Microsoft said that they have signed up 9 ISVs to add support for Entra ID authentication methods. The third-party methods work the same way as native Entra ID authentication (like the Authenticator app), meaning that verified connections can be used by other Entra solutions like Privileged Identity Management.
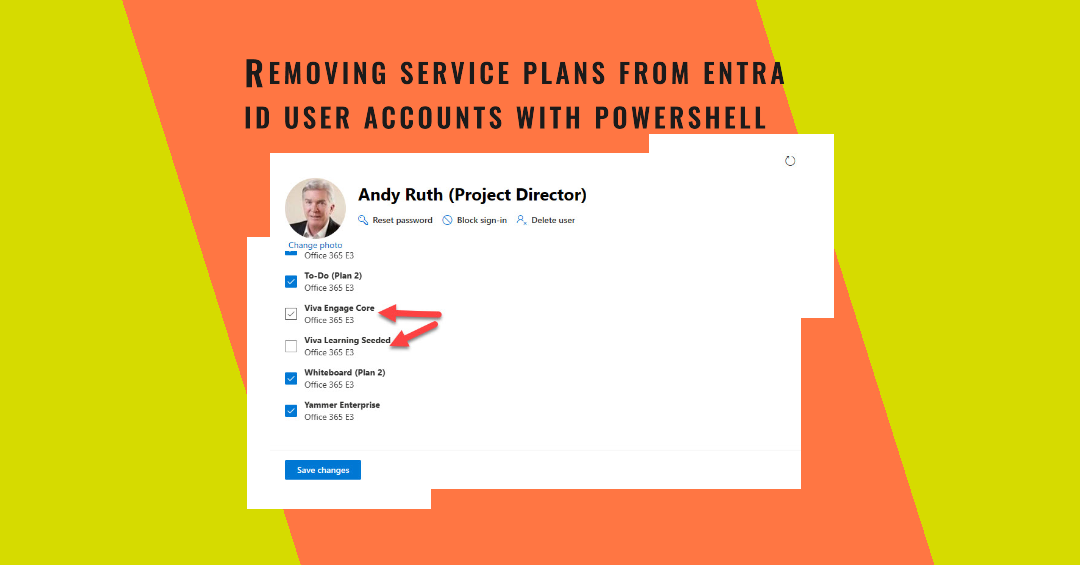
Some years ago, I wrote a script to demonstrate how to remove service plans with PowerShell. This article describes some upgrades to make the script even better by improving the code and leveraging complex Microsoft Graph queries against the license information stored for Entra ID user accounts. It’s PowerShell, so feel free to change the script!
License management is a core competence for Microsoft 365 tenant administrators. This article explains how to use PowerShell to remove licenses from accounts when an equivalent service plan is available from another license. It’s the kind of fix-up operation that tenant administrators need to do on an ongoing basis.
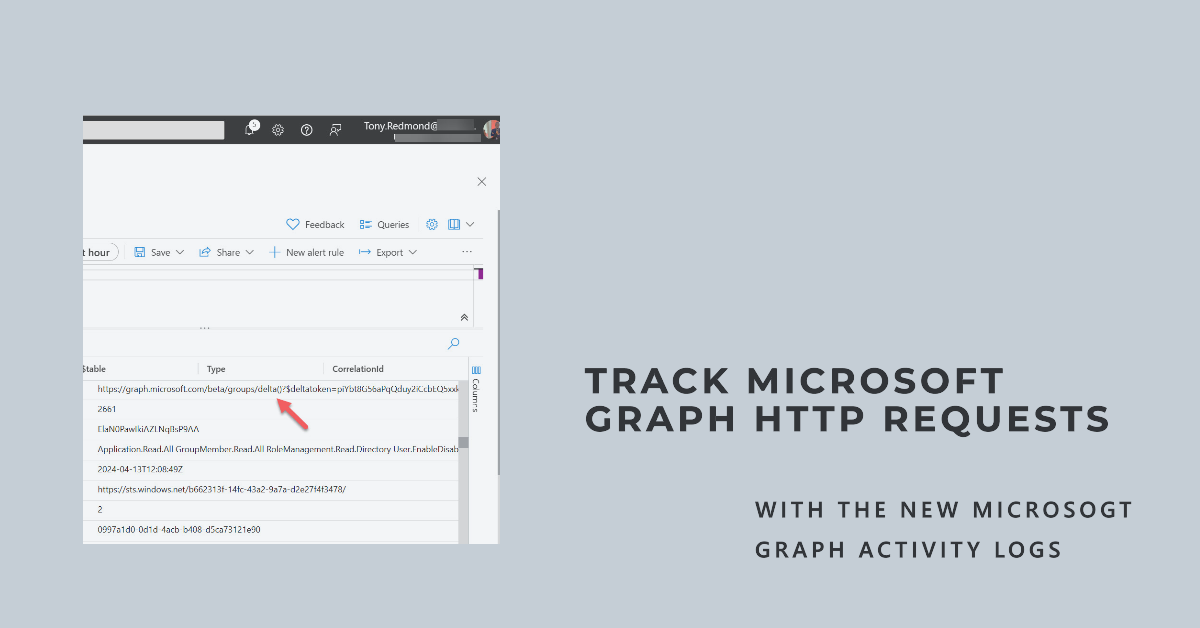
April 11 saw the general availability of Microsoft Graph activity logs, a new set of data recording details of Graph API HTTP requests made in a tenant. The logs are intended to help security analysts understand actions taken by apps in a tenant such as data access or configuration updates. Before working with Graph activity logs, security analysts will need to understand Graph API requests and the context they’re made.
The Maester tool is a community initiative to create a tool to help tenant administrators improve the security of their Entra ID tenants. It’s still in its early stages, but even so Maester shows signs that it will be a valuable asset for administrators who want to learn more about securing their tenant against possible external compromise.
A new convert to internal user preview feature allows Entra ID administrators to convert external accounts to internal accounts. An option is available in the Users section of the Entra admin center or PowerShell can be used to automate the conversion of accounts. It’s a useful feature that should prove popular.
This article describes how to use sign-in data to identify unused Entra ID registered devices. It’s an imperfect solution because Entra ID doesn’t log device information in many sign-in records. I’m sure there’s a good reason why Microsoft doesn’t capture the device information, but it’s a little frustrating. We have an imperfect and partial solution, but that’s better than nothing.
A Microsoft Technical Community article gave some interesting information about how to report soft-deleted Entra ID objects. We think we can improve the information by tweaking the script, especially to include the object type in the output. As always, you can download the script from GitHub.
Microsoft has released the preview of the Entra ID usage insights for premium license consumption. This could be the harbinger of a more restricted licensing regime for Entra ID premium features such as conditional access. Putting any barrier in place to stop more accounts being protected by multifactor authentication seems like a bad idea. Let’s hope that this isn’t the case here.
If your Microsoft 365 tenant has Entra P2 licenses, you can use the Entra Identity Secure Score feature to measure your tenant against Microsoft benchmarks and recommendations, including expiring app credentials. The fact that credentials expire is one of the reasons why I don’t use apps as much any more. Using the Microsoft Graph PowerShell SDK is just easier.
If conditional access policies impose MFA for all cloud apps, it gives external users a problem when they use Outlook desktop to read protected email. The issue is because Outlook can’t obtain a use license to decrypt the content because it can’t satisfy the MFA challenge. It’s an example of how two good parts of the Microsoft 365 ecosystem clash.
This article explains how to check Managed Identity permissions, or rather the set of consented Graph and other permissions held by the service principals used for managed identities. These can become highly permissioned over time, and that’s why checking periodically is a good idea.