Microsoft has announced the removal of events alerts from the Purview Audit solution. Fortunately, the decision doesn’t affect activity alerts. Audit-based activity alerts are a way for tenants to mark events that they want to be notified about through email when these events appear in the unified audit log. Although they remain available, better ways exist to monitor critical audit events. The only problem is deciding which approach to take.
The unified audit log is full of interesting information about who did what and when they did it. In this article, I describe how to use file operations audit events to find the last accessed date for documents in a SharePoint Online site. It’s data that isn’t available in the Microsoft Graph, but it is in the unified audit log.
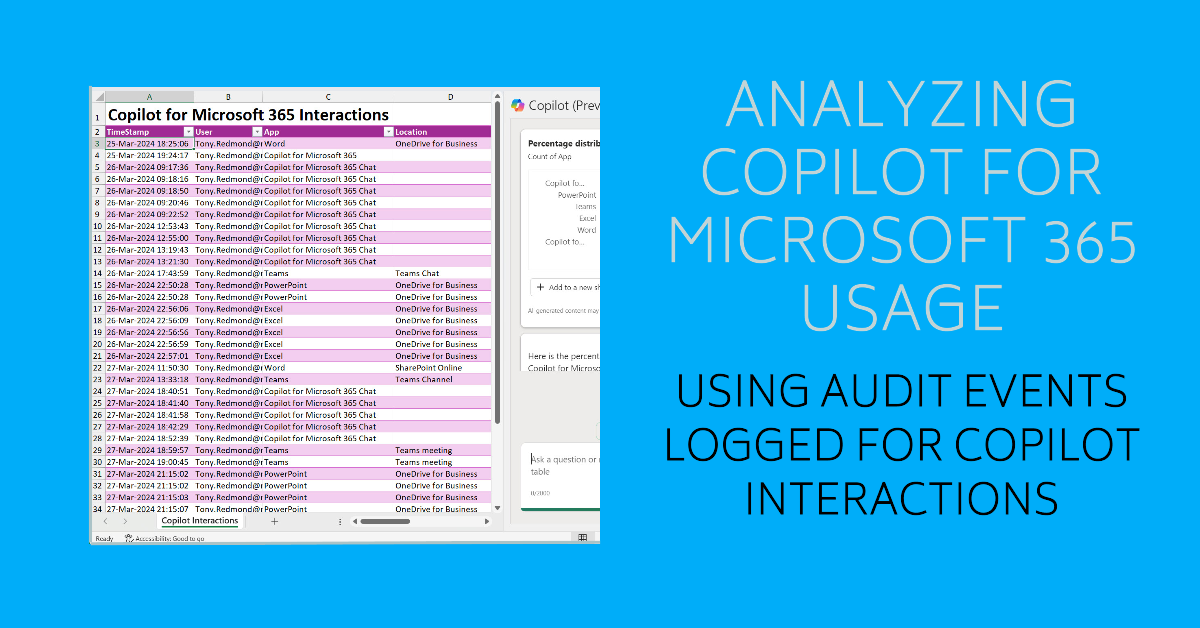
The unified audit log includes Copilot for Microsoft 365 audit events captured when users interact with Copilot through apps. The information is very helpful in terms of understanding the usage of Copilot in different apps (apart from Outlook, which isn’t captured). Some care needs to be taken to understand the data and interpret the audit events, but that’s usual when dealing with Microsoft 365 audit data.
Entra ID administrative units are supported for granular access to the Microsoft 365 audit log. Exchange Online manages the audit log so it’s core to the support. This article reviews how to restrict access to the audit log using compliance roles and RBAC and how administrative unit data is stamped onto audit events during ingestion to support restricted searches based on administrative units.
Microsoft has described the compliance support from Purview solutions for data generated by Microsoft 365 Copilot prompts and responses. There’s nothing earthshattering in terms of what Microsoft is doing, but it’s good that audit events and compliance records will be gathered and that sensitivity labels will block Copilot access to confidential data.
A question about how to report specific changes to Teams memberships gave another excuse to use PowerShell with the unified audit log to deliver a solution. The idea is that you can check audit log entries to see when specific user accounts join the membership of Teams. Once you’ve found that data, it’s a simple matter of creating email to share the results. All done with a few lines of PowerShell…
For years, I have scanned the audit log to find FileDeleted events to report deletions of SharePoint and OneDrive documents. Now, FileRecycled audit events are used instead. This wouldn’t be a problem if Microsoft had told customers, but not a trace can be found to let organizations know that the audit data they use for compliance operations has changed. I don’t know if this is the only activity name change, but given that one update has happened (and for a relatively important audit event), it’s likely that others lurk in the undergrowth.
Exchange Online organizations configured with multiple geos (satellite regions) still find it problematic to search for mailbox audit events. Microsoft might have fixed the problem for admin audit events, but mailbox audit events are often more important.
Audit records are a great way to gain an understanding of what happens inside Office 365. We use PowerShell to report actions taken with sensitivity labels such as protecting files and containers. The latest development is the addition of support in the Microsoft 365 apps for enterprise (Office desktop) to log audit events when users interact with sensitivity labels. Unsurprisingly, more events are often logged by the desktop apps than their online equivalents.