The old Set-MsolCompanySettings cmdlet is no more, so how can a Microsoft 365 tenant block email-based subscriptions? With the Graph, of course! Seriously, there’s no 1-to-1 mapping from the old cmdlet to a new, but some of the settings are available in the Entra ID authorization policy. We can update the authorization policy with PowerShell to block email-based subscriptions, like Copilot Studio.
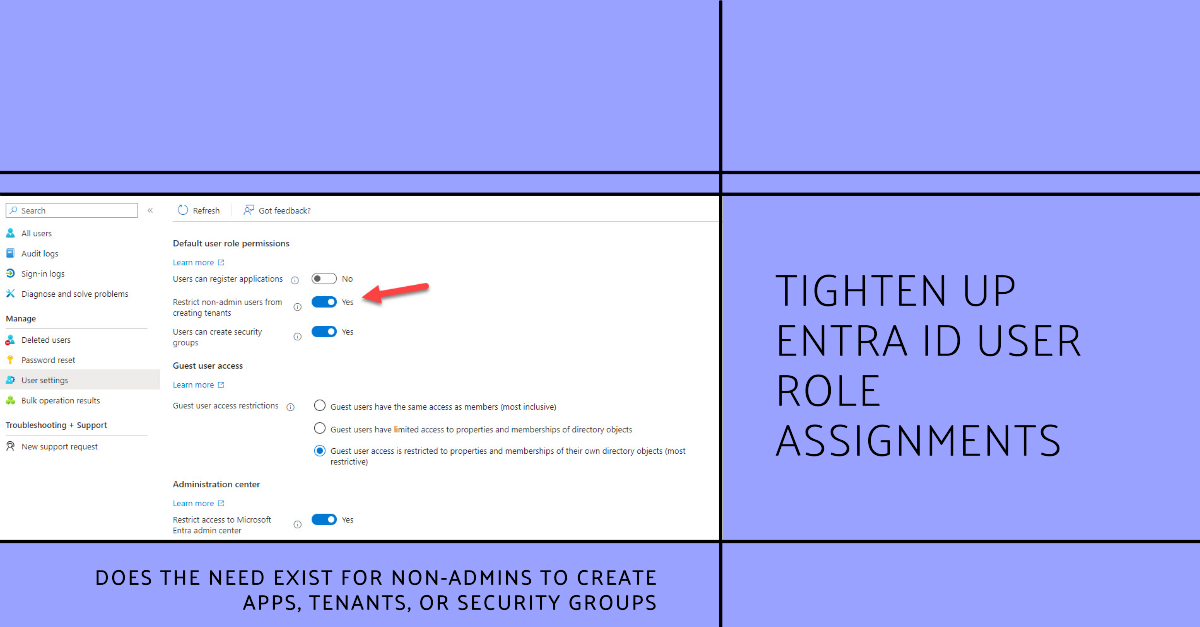
The user authorization policy defines user role permissions, or actions that non-admin users can take within an Entra ID tenant. The default settings are silly. I can’t think of good reasons to allow non-admin users to create new registered apps, tenants, or security groups. Why default settings allow these actions is a mystery, and it could be they’re just outdated.
A fuss erupted about the Azure AD admin center setting to control Azure AD tenant creation by users. Allowing people to have their own tenant can be a good thing, especially for developers who want to have a tenant as a sandbox to test code in. In this article, we discuss what the control is, what it does, and how to set it with PowerShell.